We’ll help you run a successful election
Whether you are running a simple election with a single ballot or a complex election with many ballots, we understand the stakes are high and we’ll help you succeed, with our secure online voting system.

Key benefits
Increased voter turnout
Our clients report significant increases in voter turnout. Voters love the convenience of online voting, and reminders are sent to voters who have not voted.
Save time and money
Run secure online elections and avoid the cost and effort of traditional voting methods. Voters can vote from anywhere on any device. Results are known instantly.
Worry-free election administration
Our easy to use secure online voting system has all the security features and embedded best practices to ensure your election’s success. We’ll support you all the way.
Managed or Self-Managed
We can manage your election for you, or you can choose our self-managed service.
Why BigPulse?
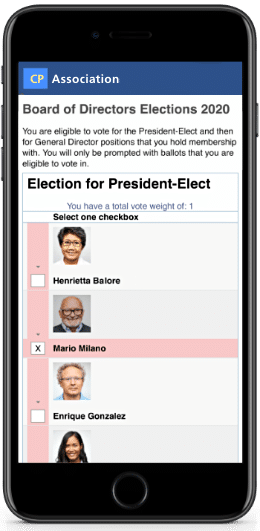
BigPulse is a global leader in delivering solutions for secure online elections and nominations.
Trusted by over 1,000 customers
We have conducted more than 500 polls since we started and BigPulse has impressed us with its thoroughness and sophistication.
This was our first online vote and BigPulse helped make it easy for us with their advice, support and flexibility. Our voters said that the site was quick and easy to use.



















